Blog
Data Security | How Secure Is Your Data?

As we enter October, internationally known as Cybersecurity Awareness Month, have you considered how secure your data is? All companies have data. Therefore, every company is also a potential hacking target. Yes, that includes your own company. And no, it isn't ‘highly unlikely’. You might think your company's data has no worth to others. Believe me, seasoned hackers may target you too. That’s why it’s important for you to identify all the risks. This enables you to take the necessary measures to ensure that your data will be as secure as possible. Exact, too, prioritises data security. In this article, I’ll tell you about the roadmap we use, which you can easily apply to your own business.
1. What risks are lurking?
Start by identifying what data is available at your company. I'm referring to data in the broadest sense: from engineering drawings to customer details and information about strategic suppliers. Now consider the reasons someone might want that data and how they could make use of it. Perhaps they could combine it with other data to make it more valuable?
2. Who might attack me?
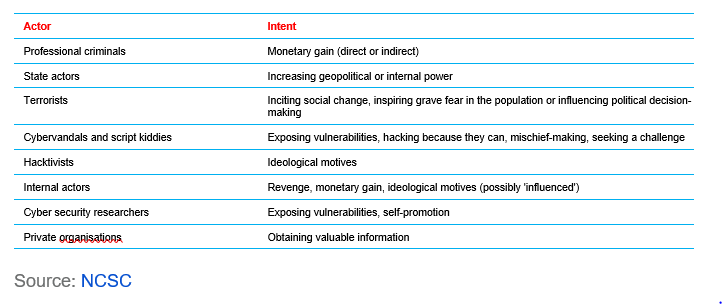
Once you have identified the risks, consider who has the potential to attack you. The Dutch National Cyber Security Centre (NCSC) distinguishes eight types of actors, each with their own motives. Which ones you must take into consideration will depend on the type of company you are and the type of data you possess. At Exact, for example, internal actors and script kiddies are the most likely.
3. How can I secure my data?
Within a company, you use various systems that store data. Your final step is to determine if additional security is required and how to implement it for each system. Once you have all that mapped out, you can draw up your actual data security action plan. In this way, you can reduce the risk to an acceptable level for you as an entrepreneur. In an ideal world, you'd like to be able to secure all your data and systems. In practice, this won't be feasible; no company anywhere secures all its data and systems. So, start with your most important data and systems.
Data security is something you should be thinking about constantly. Schedule moments of evaluation at least annually, or even more frequently if your organisation is growing fast.
Data Security: The Biggest Threats in Actual Practice
Don't worry, the average SME generally needn't fear large-scale (distributed denial-of-service) DDoS attacks. However, that doesn't mean you aren't at risk of a data breach. After all, there are quite a few other data security risks you will still need to take into account in actual practice.
Employee passwords
Employees can access plenty of company data from their computers. Often, the only thing securing that data is the passwords they've created themselves. Unfortunately, such passwords can be very simple to crack. They may include personal information or even the company name. Additionally, the same passwords are often used to access multiple systems. “Easier to remember,” is the reasoning. True, but it also makes them easier to crack!
That's why you should make sure your employees use a password manager. Then they will have only one (preferably very complex) password to remember, while all other passwords are created and updated automatically. This method is much safer.
Make use of two-factor authentication (2FA) as well. This involves the addition of another step to verify the user's identity besides a password - entering a code received by text message for example. 2FA is particularly important for access to your email. After all, changing the password to any system generally involves a ‘password recovery email’.
Servers that aren't updated
While companies cite all kinds of reasons not to update their servers automatically, this is extremely important. A server that is updated regularly will have better protection against hackers. Make arrangements with your suppliers and whoever is responsible for this in-house. Maintain good hygiene and have your routers and Wi-Fi systems checked at least once every six months. Are the protocols you use for these still secure? Do the passwords require updating?
Free tools
Pay attention to where you store your data. There is no such thing as a free lunch. If you use a free service such as Dropbox to store your data, be aware of their underlying revenue model, metadata analysis for example. These types of companies sell that data to other parties in order to make money without violating legal restrictions. Don't use free services for sensitive data. Instead, opt for paid services or systems within your own environment that remain within your own control.
This applies to storage options, but also to communication tools. For example, the free Houseparty service is currently a popular choice for video chats. What many people don't realise is that when you agree to the general terms and conditions, you give them permission to copy your contacts from your laptop or phone. Furthermore, Houseparty may use your video images for commercial purposes. Pay close attention to which applications you use and always consider the risks first. Sources such as the European Data Protection Board (EDPB) have relevant tips on their websites.
Phishing
Phishing emails and phone calls may be the most well-known form of internet fraud. Though we are all convinced we won't fall for them, phishing attempts are still one of the biggest causes of data breaches. That’s not surprising, as phishers are getting smarter and slyer. More and more phishing takes place via Whatsapp these days, asking you to transfer some money for example. Alert your employees to such practices and explain how to respond to suspected phishing attempts.
Insecure data handling (teleworking)
Many employees are now working remotely regularly. Make sure they do so safely. If an employee is accustomed to work in a public space, make it clear to them that they mustn't leave their laptop or company documents unattended during toilet breaks. And if they work while travelling by public transport, ensure that their screen has a privacy filter. For those with malicious intentions, a glimpse of a screen may be enough. Also, use a VPN so you can be sure your connection is secure.
Preparation Is Half the Battle
In conclusion, be aware of data security risks and do your best to protect your company as well as you can. Because yes, your data may also be valuable to others. You must therefore pay sufficient attention to data security and define a concrete action plan. This way, you can reduce your risk of data breaches.



